Wide Area Network (WAN)
A network that extends over large geographic areas. WANs are used to connect geographically separate LANs.
Related
Link to original
Note
The Internet itself can be considered a type of WAN, however the term ‘WAN’ is typically used to refer to an organization’s private connections between their various facilities/properties.
There are a large number of WAN technologies that have been used throughout history. Some technologies may be considered legacy in one location, yet still commonly used in another.
Example
While this topology is similar to the ‘star’ topology we mentioned in LAN Architectures, in the context of WANs they are more commonly called ‘Hub and Spoke’ topologies. In this example the Data Center is the hub and each of the offices are spokes. The connections are ‘Leased Lines’
Leased Lines
Leased Lines are dedicated physical connections between two locations. They use serial connections (PPP or HDLC). There are several Leased Line standards, offering different speeds and available in different countries. In America, standards are labeled with ‘L’s e.g. ‘L1’, ‘L2’, ‘L3’.
MPLS
Multi Protocol Label Switching (MPLS) networks are shared infrastructure similar to the Internet. Many customers, usually all enterprises, connect to and share the same infrastructure. ‘Label Switching’ allows VPNs to be created through the use of labels.
Router Types
- CE Router = Customer Edge router
- PE Router = Provider Edge router
- P Router = Provider Core router
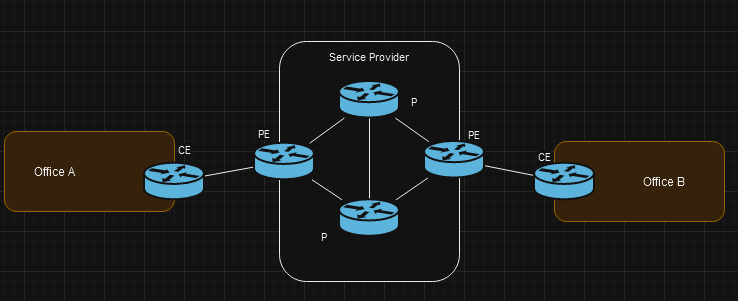
When PE routers receive frames from the CE routers they add a label to the frame. These labels are used to make forwarding decisions, not destination IP.
The CE routers do not actually use MPLS. MPLS is only used by the PE & P routers.
When using a Layer 3 MPLS VPN the CE and PE routers peer using OSPF (for example, it could be any routing protocol) to share routing information. This way the CE routers will learn routes to other CEs that are on the other end of the MPLS.
When using Layer 2 MPLS VPN the CE and PE routers do not form peerings. The service provider network is entirely transparent to the CE routers. As far as they know they are directly connected to each other; their interfaces will even be in the same subnet. As a result, the two CEs can form OSPF peerings with each other.
If a routing protocol is used then the CE routers will peer with each other directly.
Many different technologies can be used to connect to a service provider’s MPLS network (e.g. Ethernet, Fiber optic, serial, cable, wireless).
Internet Connections
Enterprises are able to connect to Internet service via the same technologies as consumers (home Internet), e.g. CATV, DSL. Enterprises also have private WAN technologies, like the aforementioned leased lines and MPLS VPNs, which can be used to access an ISP’s Internet services.
Fiber optic Ethernet has been popular in the Enterprise space for many years, and it continues to grow in popularity for both enterprise and consumer use. This is due to its high speeds, long range, and (relatively) affordable cost compared to other technologies.
Digital Subscriber Line (DSL)
DSL provides Internet connectivity to customers over traditional PSTN phone lines. This was very convenient when home Internet access was in its earlier years, as many homes already had telephone access; there was no need to install new infrastructure.
A DSL Modem was necessary to convert IP traffic to a medium suitable for transmission over phone lines.
Cable Internet
Cable Internet provided Internet access over the same CATV (Cable Television, not Category 5) network commonly used for TV service. Like DSL, a cable modem was/is required to convert data into a suitable format.
Redundant Internet Connections
Losing Internet access in the home, while annoying, isn’t usually disastrous. For many companies and organizations, however, an Internet connection is absolutely essential to their operation. Because of this it is often best practice to have multiple redundant Internet connections.
A network with a single connection to a single ISP is called Single Homed. A network with two connections to a single ISP is called Dual Homed. A network with one connection to each of two ISPs is Multihomed. A network with two connections to each of two ISPs is Dual Multihomed.
Obviously, maintaining Internet service with multiple ISPs, as well as purchasing and maintaining the hardware for multiple redundant connections can be expensive. Particularly at an enterprise level. Because of this it is important to know how much redundancy is necessary for a given enterprise, and how much is overkill.
Internet VPNs
Virtual Private Network (VPN)
Private WAN services provide security either by tagging traffic so only authorized groups can access it, or the security is built-in by merit of the fact that traffic is being transmitted on private lines that nobody else has access to.
However, when using the Internet as a WAN there is no built-in security. Unless countermeasures are taken, it would be fairly easy for anyone to intercept and view traffic.
One way we can secure data transmissions over the Internet with with Virtual Private Networks (VPNs)
Let’s talk about two particular kinds of VPN:
- Site-to-site IPsec VPNs
- Remote-access TLS VPNs
Site-to-Site VPNs (IPsec)
A site-to-site VPN spans between two devices, connecting them together over the Internet.
In IPsec, packets are fully encrypted before transmission so that they cannot be read by anyone without the encryption keys. Then the encrypted packet is encapsulated with a VPN header and a new IP header, before being transmitted to the other device. This point A to point B stream of encrypted packets — data that nobody can meaningfully access — is called a ‘VPN tunnel’.
Note
Being a point-to-point connection, IPsec does not support broadcast or multicast traffic. Therefore, routing protocols like OSPF cannot be used over tunnels. This problem can be solved with GRE over IPsec (next section)
Note
Configuring a full mesh of IPsec tunnels would be labor intensive. There are solutions to this problem as well, e.g. Cisco’s DMVPN.
GRE over IPsec
Generic Routing Encapsulation (GRE) creates tunnels like IPsec, but it does not encrypt the packets, therefore it is not secure.
That said, it can encapsulate a variety of Layer 3 protocols and broadcast and multicast messages.
GRE over IPsec gives us the best of both worlds; we can encapsulate many kinds of data with a GRE header, then encrypt it and transmit it securely.
DMVPN
Dynamic Multipoint VPN (DMVPN) is a Cisco-proprietary solution to allow routers to dynamically create a full mesh of IPsec tunnels without having to manually configure them one-by-one.
The engineer/admin does still need to manually configure some of the tunnels.
- First all routers need to be configured to tunnel to a single router, the hub site.
- The hub router then gives each other router information to form IPsec tunnels with each of the other routers.
- While this means that multiple tunnels must still be manually configured, you can potentially avoid manually configuring the majority of tunnels in the network.
Remote-Access VPNs
Remote-access VPNs are used to allow end devices to access a company’s internal resources securely over the Internet. Remote-access VPNs typically use Transport Layer Security (TLS).
VPN client software (e.g. Cisco AnyConnect) is installed on end devices (e.g. company laptops) that employees use to work remotely. With this software, the devices can form a secure tunnel to one of the company’s routers/firewalls acting as a TLS server.
Link to original